How does Dark Web works? Security and Hacking concepts for Product Manager
1. How can criminals hold your computer for Ransomware?
Ransomware is a type of malware that can damage your computer; it is a piece of software code that locks or encrypts your important files until you pay the amount demanded by hackers. This type of malware comes via email or as an attachment to download. It exploits a flaw in the operating system and runs malicious code on your computer. Once this runs on your computer, it locks all your files and gets decrypted only when you pay the amount.
They take money in bitcoins through a specialized wallet that doesn’t store any kind of information. This ensures that their information is hidden from the government.
How can you prevent ransomware?
One of the most effective ways to protect from this kind of malware is to have high-security encryption in the operating system. Large organizations like hospitals, governments etc., are at high risk, so they should spend a great amount of money on their IT infrastructure. Another solution is to do a backup of your files to always restore the recent version.
How do people sell drugs online? What does it mean by dark web?
In 2013, the US government banned a website called Silkroad because it is a kind of amazon for illegal things like drugs, fake passports, guns etc. So how do these markets work? We are going to explore this.
Deep and Dark Web
People who are on the platform are anonymous because if police or government know their association with these things, then there are high chances of getting caught. But this is not enough; Computer’s unique IP address is also sufficient to track them down. So they use it with the help of the deep web.
The deep web includes information on the internet that you cannot find using google search. The deep web is 1000 times bigger than the clear web. The dark web is the subset of the Deep web that you can’t access without special software to encrypt all the information and anonymize your IP address.
Accessing the Dark Web
As mentioned, you need to have special software to use the dark web, one of the most commonly used software to visit the dark web is TOR (commonly known as The Onion Router). TOR wraps your information and communication in layers of encryption and bounces it around through different servers. Each of which knows only information like where it is coming from and where it is going, which makes it difficult to track. Marketplaces that are on the Dark web use Bitcoins as a currency.
How can public Wi-Fi steal your money?
Let’s take an example that while working, you go to Starbucks and realize that you need to connect to the Wi-Fi to send some email or see your bank statement. You see a public Wi-Fi and connect to the public Wi-Fi, boom your account got debited. Hackers often set up phony Wi-Fi which is designed to look like legitimate networks and try to dupe people into connecting to them. If you connect to a hacker’s network, that hacker’s route sits between you and every website you want to connect to, so it can read every bit of information being sent back and forth.
You might be wondering what about HTTPS? Doesn’t it encrypt communication?
Yes, it does, but hackers nowadays can use SSLStrip, which can fool your computer into talking with a server with HTTP instead of HTTPS. If you request a bank statement via net banking, then a hacker might steal your password and username and can use it to steal the money. So don’t blindly connect to the Public Wi-Fi. Instead of this, you can use a VPN server which can turn the public Wi-Fi into a private one by encrypting all the information.
To summarize, how could a public Wi-Fi network help someone steal your identity? Well, if a hacker got you to connect to their network and used SSLStrip, they could make a man-in-the-middle attack to get your passwords and other identifying information. That way, they could steal your identity without you even knowing! As we mentioned in this last section, the best way to fight back against these man-in-the-middle attacks is to use a VPN.
How does WhatsApp encrypt your message so thoroughly that even it can’t read them?
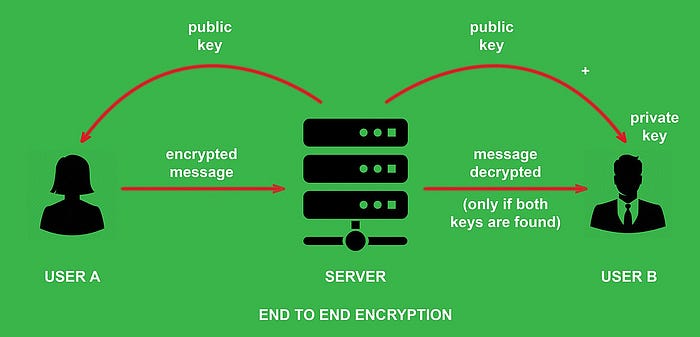
WhatsApp is being praised a lot for its end-to-end encryption, such that the message is only seen to the sender and receiver; even WhatsApp can’t read it. Let’s see how does the end-to-end encryption of WhatsApp works. To understand this, let’s assume you have to send a package to your friend through a postal service, but your postal service always sees the thing you are sending to your friend. Since you have no alternative other than opting for a postal service, you have to come up with some smart techniques.
You create a key and hundreds of locks that can be opened with that key. You kept the key with you and distributed the lock around the country so that anyone could have this lock. So, when anyone wants to send you a message, he uses the lock which the key at your home can open. This way you have secured the system and it’s so clever that anyone can send any a stuff worrying about anything, and you can only encrypt the message because you have the key.
This is how end to end encryption works; every user is given a “public key” (which, in our example, is a lock) and a “private key” (which is a private key in our example). Every message is encrypted using the recipient’s public key and can only be decrypted using their private key and some math. All the encryption and decryption is done on users’ devices, so the app makers can’t decrypt messages.


Comments
Post a Comment